sendmail에서 메일을 기본으로 보낼땐 25포트를 사용하고 SSL을 이용해서 보내면 465번을 포트를 이용해서 TLS 버전을 이용해서
보낼수 있다
o/s : centos 7. / rocky 8.x
1. senmmail / sendmail-cf 설치
|
1 |
[root@xinet ~]# yum -y install sendmail sendmail-cf |
2. sendmail 에서 사용할 인증서 openssl를 이용해서 인증서 설치
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 |
[root@xinet ~]# mkdir /etc/mail/certs/ [root@localhost ssl]# openssl genrsa -des3 -out mail.xinet.kr.key 2048 Generating RSA private key, 2048 bit long modulus (2 primes) ..............+++++ ..............................................................................+++++ e is 65537 (0x010001) Enter pass phrase for mail.xinet.kr.key: Verifying - Enter pass phrase for mail.xinet.kr.key: [root@localhost conf]# openssl req -new -key mail.xinet.kr.key -out mail.xinet.kr.csr Enter pass phrase for mail.xinet.kr.key: You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:KR State or Province Name (full name) [Some-State]:Gyeonggi-do Locality Name (eg, city) []:Gwangmyeong-si Organization Name (eg, company) [Internet Widgits Pty Ltd]:xinet Organizational Unit Name (eg, section) []:se Common Name (e.g. server FQDN or YOUR name) []:mail.xinet.kr Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: |
3. 인증서를 발급을 받았으면 해당 디렉토리 /etc/mail/certs 폴더에 인증서를 업로드 및 권한 600으로 설정
|
1 2 3 4 5 6 7 8 |
[root@xinet /etc/mail/certs]# chmod 600 /etc/mail/certs/* [root@xinet /etc/mail/certs]# ll 합계 16 -rw------- 1 root root 2002 4월 5 10:28 CA_GLOBALSIGN.crt -rw------- 1 root root 2014 4월 5 10:28 ChainFile_ChainBundle.crt -rw------- 1 root root 2278 4월 5 10:28 mail.xinet.kr.crt -rw------- 1 root root 1675 4월 5 10:28 mail.xinet.kr.key |
4. sendmail 에서 인증서를 사용할수 있게 sendmail.mc파일 수정
|
1 2 3 4 5 6 7 |
[root@xinet /etc/mail/certs]# vi /etc/mail/sendmail.mc define(`confCACERT_PATH', `/etc/mail/certs')dnl define(`confCACERT', `/etc/mail/certs/CA_GLOBALSIGN.crt')dnl define(`confSERVER_CERT', `/etc/mail/certs/mail.xinet.kr.crt')dnl define(`confSERVER_KEY', `/etc/mail/certs/mail.xinet.kr.key')dnl DAEMON_OPTIONS(`Port=smtps, Name=TLSMTA, M=s')dnl |
5. sendmail.mc 파일을 cf 파일로 변경
|
1 |
[root@xinet /etc/mail/certs]# m4 /etc/mail/sendmail.mc > /etc/mail/sendmail.cf |
6. sendmail 서버 새시작
|
1 |
[root@xinet /etc/mail/certs]# systemctl restart sendmail |
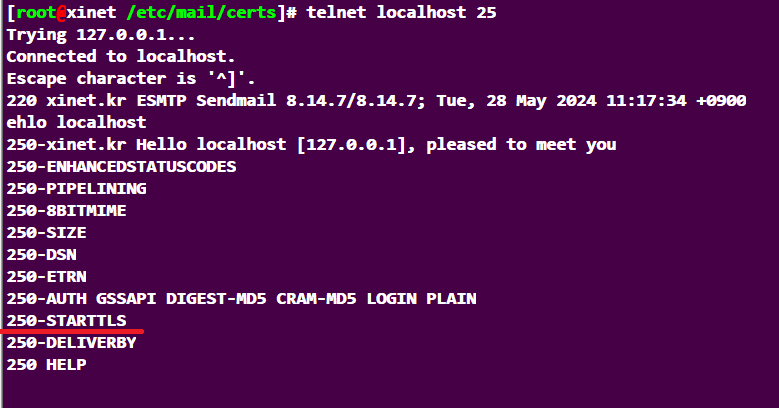
7. telnet 명령어로 확인 telnet localhsot 25 입력후 메시지 창에 ehlo localhost 입력
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 |
[root@xinet /etc/mail/certs]# telnet localhost 25 Trying 127.0.0.1... Connected to localhost. Escape character is '^]'. 220 xinet.kr ESMTP Sendmail 8.14.7/8.14.7; Tue, 28 May 2024 11:17:34 +0900 ehlo localhost 250-xinet.kr Hello localhost [127.0.0.1], pleased to meet you 250-ENHANCEDSTATUSCODES 250-PIPELINING 250-8BITMIME 250-SIZE 250-DSN 250-ETRN 250-AUTH GSSAPI DIGEST-MD5 CRAM-MD5 LOGIN PLAIN 250-STARTTLS 250-DELIVERBY 250 HELP |
메일 폼을 이용해서 php통해서 보내면
|
1 2 3 4 5 6 7 8 9 10 11 |
// 환경설정 - 기본 $config = array( 'host'=>'ssl://mail.xinet.kr', // SMTP 호스트 주소 'smtp_id'=>'server@xinet.kr', //SMTP 아이디 'smtp_pw'=>'123412343412341234', //SMTP 비밀번호 'port'=>'465', //SMTP 포트 'debug'=>1, // 디버그 , 0: 미사용, 1: 사용 'msg'=>1, // 메시징뷰 , 0: 미사용, 1: 사용 'charset'=>'UTF-8', // SMTP 언어셋 'ctype'=>'text/html', // SMTP 내용 컨텐츠타입 ); |
메일로그
|
1 2 3 4 |
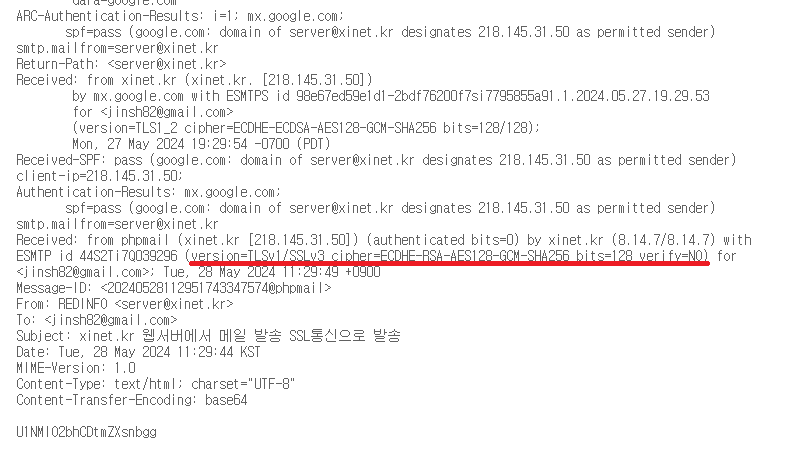
May 28 11:29:50 xinet sendmail[39295]: 44S2TiM2039295: from=<server@xinet.kr>, size=0, class=0, nrcpts=0, proto=ESMTP, daemon=TLSMTA, relay=xinet.kr [218.145.31.50] May 28 11:29:52 xinet sendmail[39296]: 44S2Ti7Q039296: from=<server@xinet.kr>, size=375, class=0, nrcpts=1, msgid=<20240528112951743347574@phpmail>, proto=ESMTP, daemon=TLSMTA, relay=xinet.kr [218.145.31.50] May 28 11:29:53 xinet sendmail[39311]: STARTTLS=client, relay=gmail-smtp-in.l.google.com., version=TLSv1/SSLv3, verify=FAIL, cipher=ECDHE-ECDSA-AES128-GCM-SHA256, bits=128/128 May 28 11:29:55 xinet sendmail[39311]: 44S2Ti7Q039296: to=<jinsh82@gmail.com>, ctladdr=<server@xinet.kr> (1014/1014), delay=00:00:06, xdelay=00:00:03, mailer=esmtp, pri=120375, relay=gmail-smtp-in.l.google.com. [74.125.203.27], dsn=2.0.0, stat=Sent (OK 1716863395 98e67ed59e1d1-2bdf76200f7si7795855a91.1 - gsmtp) |
TLSv1/SSLv3 보낸것을 확인할 수 있다
tls 버전이 낮아서 그렇고 버전이 높게 해서 구성하면 tls 1.2로 표시되 된다
openssl 명령어로도 확인 가능
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 |
[root@xinet ~]# openssl s_client -connect mail.xinet.kr:465 -crlf CONNECTED(00000003) depth=2 OU = GlobalSign Root CA - R6, O = GlobalSign, CN = GlobalSign verify return:1 depth=1 C = BE, O = GlobalSign nv-sa, CN = GlobalSign GCC R6 AlphaSSL CA 2023 verify return:1 depth=0 CN = mail.xinet.kr verify return:1 --- Certificate chain 0 s:/CN=mail.xinet.kr i:/C=BE/O=GlobalSign nv-sa/CN=GlobalSign GCC R6 AlphaSSL CA 2023 1 s:/C=BE/O=GlobalSign nv-sa/CN=GlobalSign GCC R6 AlphaSSL CA 2023 i:/OU=GlobalSign Root CA - R6/O=GlobalSign/CN=GlobalSign --- Server certificate 생략 Acceptable client certificate CA names /C=BE/O=GlobalSign nv-sa/CN=GlobalSign GCC R6 AlphaSSL CA 2023 Client Certificate Types: RSA sign, DSA sign, ECDSA sign Requested Signature Algorithms: RSA+SHA512:DSA+SHA512:ECDSA+SHA512:RSA+SHA384:DSA+SHA384:ECDSA+SHA384:RSA+SHA256:DSA+SHA256:ECDSA+SHA256:RSA+SHA224:DSA+SHA224:ECDSA+SHA224:RSA+SHA1:DSA+SHA1:ECDSA+SHA1 Shared Requested Signature Algorithms: RSA+SHA512:DSA+SHA512:ECDSA+SHA512:RSA+SHA384:DSA+SHA384:ECDSA+SHA384:RSA+SHA256:DSA+SHA256:ECDSA+SHA256:RSA+SHA224:DSA+SHA224:ECDSA+SHA224:RSA+SHA1:DSA+SHA1:ECDSA+SHA1 Peer signing digest: SHA512 Server Temp Key: ECDH, P-256, 256 bits --- SSL handshake has read 3832 bytes and written 427 bytes --- New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256-GCM-SHA384 Server public key is 2048 bit Secure Renegotiation IS supported Compression: NONE Expansion: NONE No ALPN negotiated SSL-Session: Protocol : TLSv1.2 Cipher : ECDHE-RSA-AES256-GCM-SHA384 Session-ID: 94062A611864A37EDC1494385B2CBA6E70892917E651989DE4444EE36D11DE3A Session-ID-ctx: Master-Key: 920DD9EA8256621B65D60C2E7165CCE7FAD3F0D299122F4E9E10FE34B2B00E6178EB095333E420D023348FBB545DEE05 Key-Arg : None Krb5 Principal: None PSK identity: None PSK identity hint: None TLS session ticket lifetime hint: 1 (seconds) TLS session ticket: |
만약 smtp에서 ssl이 적용되어 있지 않다면
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
[root@xinet ~]# openssl s_client -connect webmail.xinet.kr:465 -crlf CONNECTED(00000003) 140335001978768:error:140790E5:SSL routines:ssl23_write:ssl handshake failure:s23_lib.c:177: --- no peer certificate available --- No client certificate CA names sent --- SSL handshake has read 0 bytes and written 289 bytes --- New, (NONE), Cipher is (NONE) Secure Renegotiation IS NOT supported Compression: NONE Expansion: NONE No ALPN negotiated SSL-Session: Protocol : TLSv1.2 Cipher : 0000 Session-ID: Session-ID-ctx: Master-Key: Key-Arg : None Krb5 Principal: None PSK identity: None PSK identity hint: None Start Time: 1716881994 Timeout : 300 (sec) Verify return code: 0 (ok) |